You Can Understand The Basics of Encryption.
The field of science known as cryptography, or “secret agent,” encompasses the encryption techniques that are currently utilized on the internet. It works by converting your transmitted data into a code that can later be “unwrapped” and decoded with the help of a discrete “key.” Predetermined formulas serve as these keys, which immediately encode your data in accordance with that formula.
The translating is finished on the opposite finish of the exchange at the point it should be perceived to handle your request, and so forth. Encryption keys make an interpretation of our data into another dialect, in a manner of speaking, so it can’t be unraveled on the way to its objective.
Principal Types of Encryption The two most widely used encryption techniques are: public-key encryption in addition to symmetric key encryption.
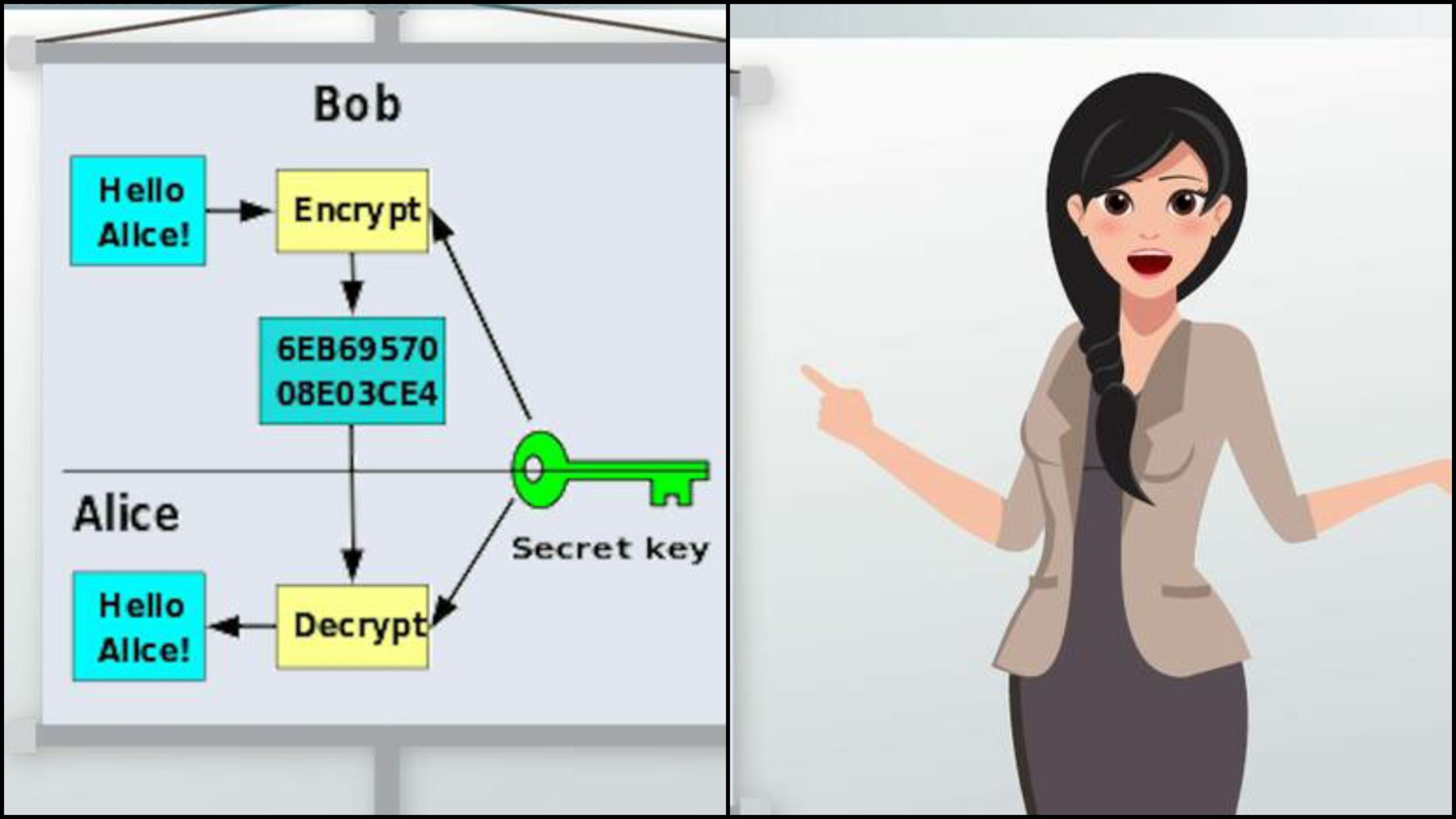
1. Symmetric-key encryption….
The High level Encryption Standard (AES) comprises of keys that have up to 256 distinct codes for every individual lump of data sent, (alpha letters, numbers, or pixels in an image). How that affects us is, a PC programmer would need to attempt a huge number of changes of code blends before the sucker could get to your data. Naturally, both the sending and receiving computers must be able to code and decode in the specified encryption format whenever any code system is utilized.
2. Information is only hidden while it is being transferred to another computer using public-key encryption.
This technique utilizes an encryption code that comprises of two different keys. The main key is a confidential key utilized by every individual PC, while the second “public key” is divided among the two PCs. Simply put, your computer codes the data that is being sent before sending an “extra code” packet containing the public key, which is used to decode the data later. The receiving computer must then translate the data into a form that can be used using its own private key and its public key to decipher the data. The bottom line is that encryption renders our information unintelligible to hackers, so we can now safely conduct online transactions.
Expert in data security and backup, Roger G. Brown He has a lot of experience helping individuals and small businesses save money on data backup and storage decisions.



Leave a Reply